
DC Sync Attack: The Art of Impersonation
In the digital era, where data flows like electricity, understanding network devices and topologies is critical to building and maintaining robust, scalable, and secure IT infrastructure. Whether it's for a small office, a large enterprise, or an industrial data center, the core architecture of any computer network begins with a set of intelligent devices and their interconnections.
Network devices are hardware units that mediate, manage, and maintain communication between nodes in a network. Each serves a distinct role in data transmission, traffic control, or access security. Let's walk through the essential ones:
A router directs traffic between different networks. Think of it as a smart postmaster that ensures data packets take the optimal route from sender to recipient. In homes, routers typically connect a local network to the internet. In businesses, they handle complex routing between internal VLANs and external networks.
Unlike routers, switches operate within a single network. They manage direct device-to-device communication using MAC addresses, ensuring that data sent from a computer to a printer, for instance, doesn't flood the whole network.
A hub is an outdated device that broadcasts incoming data to all connected devices regardless of the destination. It's simple and cheap—but inefficient and insecure—so switches have mostly replaced them.
An access point allows wireless devices to connect to a wired network. It's often integrated into routers in consumer setups but deployed separately in enterprise networks for broader Wi-Fi coverage.
A firewall filters network traffic to prevent unauthorized access. It can be a standalone appliance, built into a router, or implemented via software.
The modem modulates and demodulates signals between digital networks and analog transmission lines—essential for connecting to ISPs over DSL, fiber, or cable.
A network topology defines the physical or logical layout of a network. It influences performance, fault tolerance, and cost. Let's explore the most common ones:
All devices share a single communication line. It's cost-effective for small networks but prone to failure if the central cable is damaged.
All devices connect to a central switch or hub. It's easy to manage, and failure of a single device doesn't affect the rest—but if the hub fails, the whole network goes down.
Devices form a closed loop. Each device has two neighbors, and data flows in one or both directions. While it reduces collisions, a break can disable the whole network unless it's a dual ring.
Each device is connected to every other device. It's expensive but offers high redundancy and reliability.
Combines elements of multiple topologies, such as star-ring or star-bus, tailored to fit specific network needs.
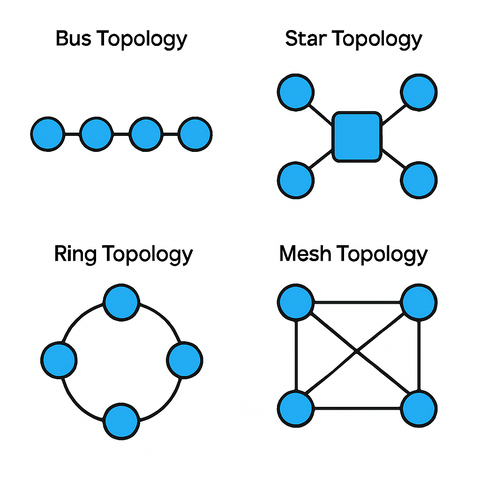
It's important to distinguish between physical topology (the actual layout of cables/devices) and logical topology (how data flows through the network). A network might be physically arranged as a star but logically function as a bus.
Understanding network devices and topologies is essential for:
The digital world relies on invisible highways of data, built from simple building blocks: routers, switches, cables—and the paths they follow. As businesses scale and cybersecurity threats evolve, mastering the structure and function of these networks is no longer just the job of the IT department—it's a critical literacy for anyone working with technology.
Want to explore more? Read our follow-up article on Securing Enterprise Networks with VLANs and Subnetting.
Love it? Share this article: