SOCKS4 vs SOCKS5: Differences from a Cybersecurity Perspective
An in-depth comparison of SOCKS4 and SOCKS5 proxies, highlighting their features, differences, and implications for cybersecurity.
Dive deep into computer networking from a cybersecurity lens. Explore essential topics like DNS, network protocols, and real-world attack and defense scenarios.

An in-depth comparison of SOCKS4 and SOCKS5 proxies, highlighting their features, differences, and implications for cybersecurity.
Learn how to design and implement network segmentation in shared business centers, ensuring isolation, compliance, and operational efficiency across multiple companies under one roof.

An in-depth article on Man-in-the-Middle (MitM) attacks, exploring their mechanisms from both offensive and defensive viewpoints, with examples, code samples, and pro tips.

A technical breakdown of Fragmentation and Aggregation Attacks (FragAttacks), a set of Wi-Fi vulnerabilities affecting WPA2, WPA3, and billions of devices worldwide.

Learn what a DMZ (Demilitarized Zone) is in networking, why it's important, and how real-world scenarios help secure IT environments.
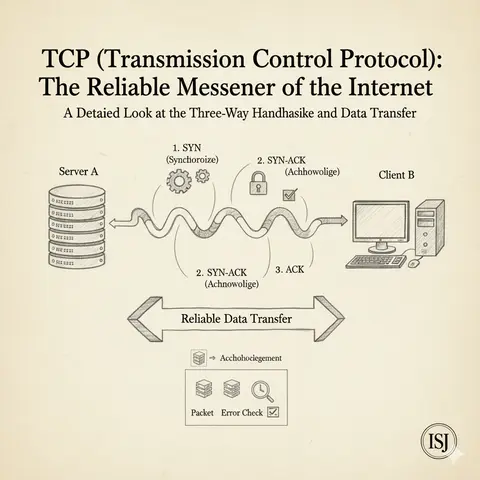
A beginner-friendly guide to TCP, the reliable protocol powering the internet, with analogies, code samples, and a cybersecurity angle.

An in-depth exploration of the Address Resolution Protocol (ARP) as defined in RFC 826, covering its core mechanisms, packet formats, and modern cybersecurity implications with red team exploitation techniques and blue team defensive strategies.

An in-depth exploration of RFC-793, the TCP specification, with a focus on its core mechanisms, red team exploitation techniques, and blue team defensive strategies.

A deep dive into Dynamic Host Configuration Protocol (DHCP), its role in networking, and how attackers and defenders approach it. Includes red and blue team perspectives with practical examples.

A comprehensive guide to host-based authentication, covering how it works, security risks, red team exploitation techniques, and blue team defense strategies.