
Wireshark: A Beginner's Guide to Network Analysis
Learn how to use Wireshark for network troubleshooting, security investigations, and protocol analysis with real-world examples.
Dive deep into computer networking from a cybersecurity lens. Explore essential topics like DNS, network protocols, and real-world attack and defense scenarios.

Learn how to use Wireshark for network troubleshooting, security investigations, and protocol analysis with real-world examples.
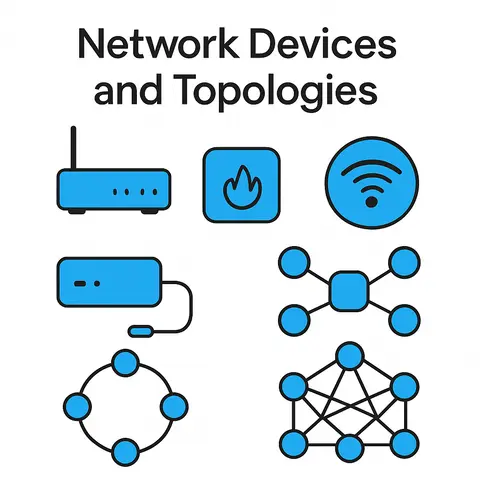
Understand the key network devices and how different topologies shape the foundation of modern communication systems.
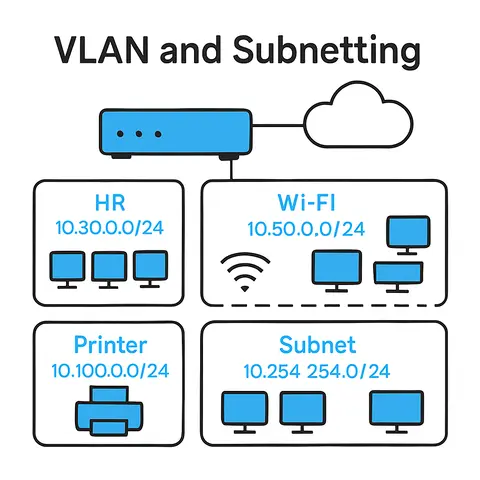
Explore how VLANs and subnetting can be used to segment, isolate, and defend enterprise networks from internal threats and lateral movement.

Explore how network protocols are the secret language of cyber warfare. Discover how Red Teams exploit them for reconnaissance and Blue Teams harden defenses for ultimate network security.

Explore WhoFi, a groundbreaking technology using Wi-Fi signals to identify individuals, and delve into its practical applications and significant ethical implications.

This article provides a high-level overview of subnetting, explaining its importance in network management and outlining common approaches to effective network segmentation.

Explore the most common network ports and their associated protocols, understanding their functions and, crucially, the typical cyberattacks that target them. Learn how knowing these default communication channels is vital for network defense and offense.
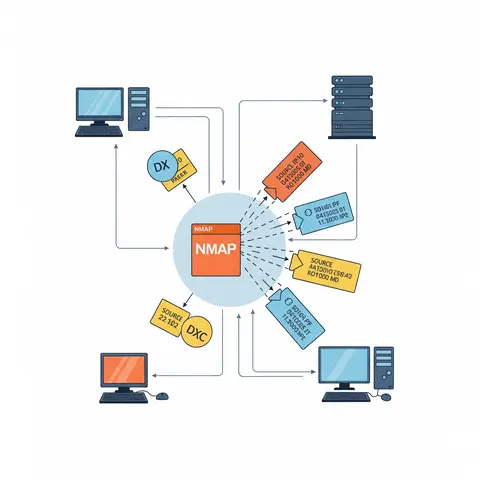
An overview article exploring the capabilities and use cases of the Nmap network scanner, highlighting its potential for network security and the inherent dangers of misuse.
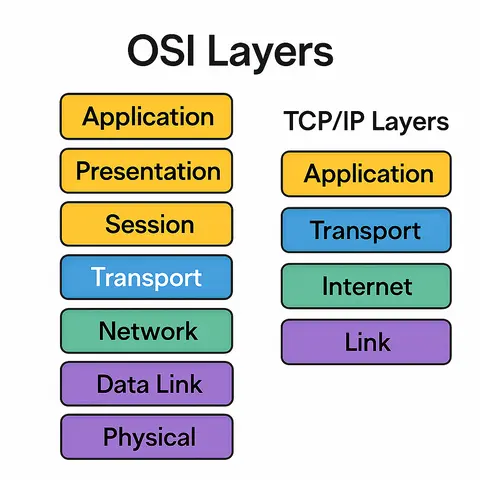
An article explaining the seven layers of the OSI model and providing examples of common cyberattacks that target each layer.