Secure Shell (SSH) Proving Methods: An Overview for Red and Blue Teams
A comprehensive guide to Secure Shell (SSH) proving methods, including authentication mechanisms, practical usage, and perspectives from both attackers and defenders.
Dive deep into computer networking from a cybersecurity lens. Explore essential topics like DNS, network protocols, and real-world attack and defense scenarios.

A comprehensive guide to Secure Shell (SSH) proving methods, including authentication mechanisms, practical usage, and perspectives from both attackers and defenders.

A detailed exploration of the TCP/IP protocol suite, its technical foundations, code samples, and cybersecurity considerations.

Learn how to find which network connections are associated with a process using basic system tools on Linux and Windows.

Learn how to secure DNS infrastructure with network segmentation and access control. Discover why authoritative and recursive DNS servers must be isolated, and see practical ACL configuration examples to prevent unauthorized DNS queries.

Learn how DNS amplification attacks weaponize open DNS resolvers to flood a victim's network. This article details the attack mechanics and provides crucial blue team strategies, including ingress filtering and DNS hardening, to defend against this powerful form of DDoS.

An in-depth guide to NXDOMAIN responses and phantom domain attacks in DNS, with red and blue team perspectives and code examples.
A beginner-friendly guide to the Domain Name System (DNS). Learn how DNS works, its hierarchy, and its critical role in cybersecurity for Red and Blue Teams.
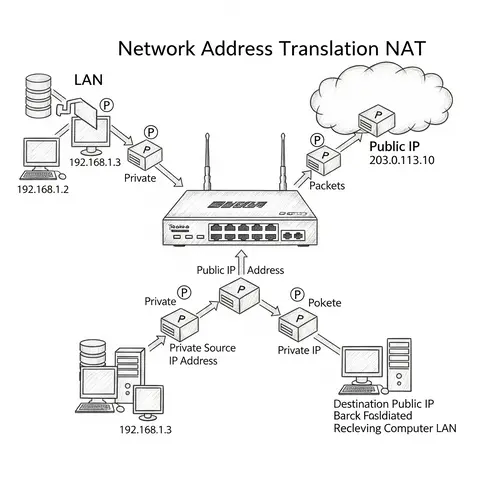
An in-depth article explaining the concept of Network Address Translation (NAT), its types, usage in modern networks, benefits, drawbacks, and security implications. Suitable for beginners and intermediate readers in networking and cybersecurity.

This comprehensive article explores the intricacies of Wireless Local Area Networks (WLANs), from their fundamental components like access points and network cards to the evolution of IEEE 802.11 standards (Wi-Fi 4, 5, and 6) and the crucial security protocols (WEP, WPA, WPA2, WPA3) that keep your data safe.

A deep dive into protocol downgrading attacks, how they work, real-world examples, and code demonstrations to help security operators understand and detect them.