
Fragment Attack (FragAttacks): A Technical Analysis
A technical breakdown of Fragmentation and Aggregation Attacks (FragAttacks), a set of Wi-Fi vulnerabilities affecting WPA2, WPA3, and billions of devices worldwide.

A technical breakdown of Fragmentation and Aggregation Attacks (FragAttacks), a set of Wi-Fi vulnerabilities affecting WPA2, WPA3, and billions of devices worldwide.

A detailed guide on what runbooks are, why they matter in IT and cybersecurity operations, and how they streamline incident response and system management.
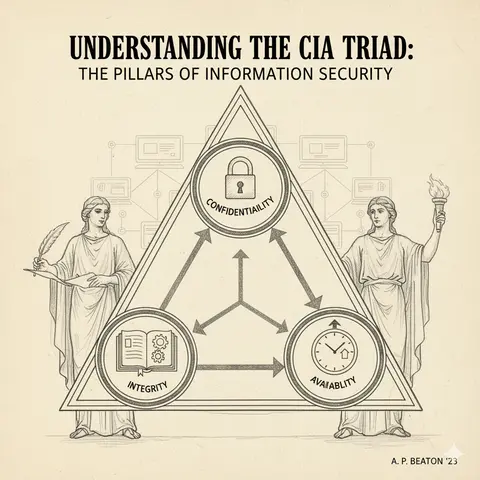
A beginner-friendly explanation of the CIA Triad—Confidentiality, Integrity, and Availability—and why it is the cornerstone of modern cybersecurity.

A deep dive into Near Field Communication (NFC), its applications in payments, security, and beyond, and what it means for businesses and consumers.

Learn how iptables works, explore practical firewall rules, and discover real-world scenarios where iptables strengthens Linux security.

Learn what a DMZ (Demilitarized Zone) is in networking, why it's important, and how real-world scenarios help secure IT environments.

A deep dive for tech pros on AI's transformative role in cybersecurity, from ML-driven anomaly detection to adversarial defenses, with code and forward-looking insights.
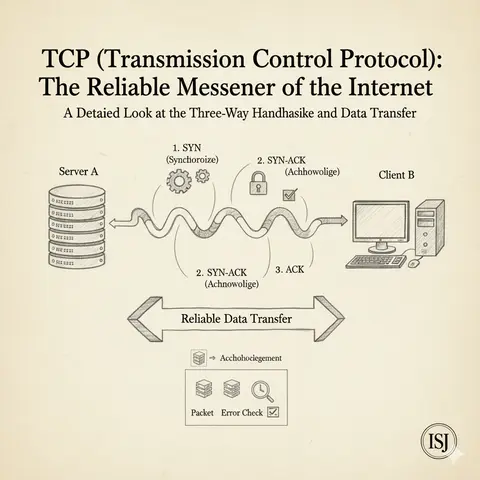
A beginner-friendly guide to TCP, the reliable protocol powering the internet, with analogies, code samples, and a cybersecurity angle.
Practical guide to scanning all ports with nmap: TCP and UDP techniques, sane command examples, and ways to reduce scan noisiness for legitimate, authorized testing.

An in-depth exploration of the Address Resolution Protocol (ARP) as defined in RFC 826, covering its core mechanisms, packet formats, and modern cybersecurity implications with red team exploitation techniques and blue team defensive strategies.