
Hacking the Cloud: Exploiting Misconfigurations and Identity Flaws
A deep dive into how attackers compromise cloud environments through misconfigurations and identity management weaknesses, with examples, attack paths, and defense strategies.

A deep dive into how attackers compromise cloud environments through misconfigurations and identity management weaknesses, with examples, attack paths, and defense strategies.

Understanding the essential legal frameworks in cybersecurity and how they guide ethical, compliant practices across industries.

A comprehensive guide for new cybersecurity professionals on understanding and practicing professional ethics in their careers.

A practical guide for cybersecurity professionals on establishing and following rules of engagement during security testing, investigations, and incident response.

A deep dive into the lsof command, its usage, examples, and best practices for Linux system administrators and cybersecurity professionals.

Explore the ifconfig command-line tool for managing network interfaces in Linux. Learn its syntax, use cases, and security considerations for both blue and red teams.
Understand the key network devices and how different topologies shape the foundation of modern communication systems.
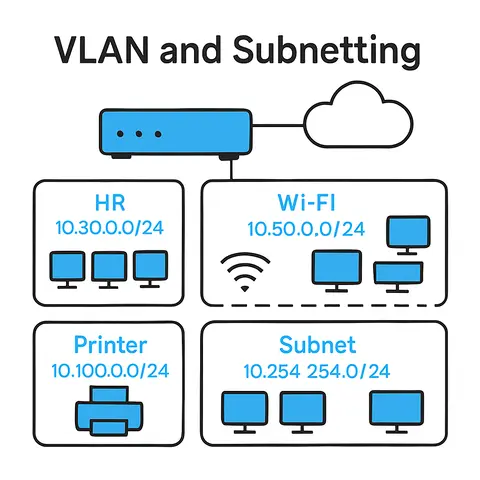
Explore how VLANs and subnetting can be used to segment, isolate, and defend enterprise networks from internal threats and lateral movement.

An investigative look at how continuous integration and deployment pipelines have become a favorite target for cyber attackers—and what organizations must do to defend them.

Exploring how attackers can exploit Git misconfigurations and leaks to infiltrate systems and extract secrets.