
Nikto Web Scanner Explained: A Practical Guide for Security Teams
An in-depth guide to the Nikto web vulnerability scanner—how it works, what it detects, limitations, and how security teams can use it responsibly.

An in-depth guide to the Nikto web vulnerability scanner—how it works, what it detects, limitations, and how security teams can use it responsibly.

An in-depth look at how attackers use AI to defeat DRM, clone live streams, and operate unauthorized mirror sites—and what content owners can do about it.

How invisible, user-specific markers help live sports broadcasters identify the source of illegal restreams and shut them down within minutes.

Hidden metadata can compromise your security. Master ExifTool, the powerful open-source utility for analyzing and editing file metadata in cybersecurity workflows.

A deep technical and executive-level analysis of MongoBleed (CVE-2025-14847), explaining the root cause, attacker workflow, real-world impact, and how organizations should patch and respond.

How small IT departments can use Grafana and Prometheus to achieve enterprise-grade monitoring, alerting, and visibility without enterprise complexity or cost.
A practical, ISO-aligned guide to the most in-demand cybersecurity skills for 2026, covering cloud security, Zero Trust, AI-driven defense, compliance, and incident response.

Learn how OpenTelemetry extends security detection beyond traditional logs by correlating traces, metrics, and context to uncover modern attack paths and control failures.
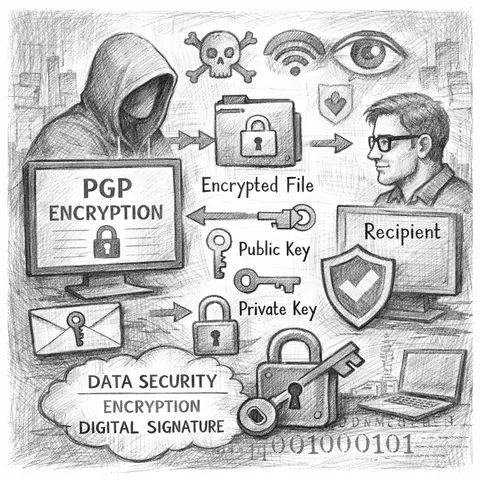
A deep dive into PGP encryption, its cryptographic foundations, real-world applications, and why it remains relevant for cybersecurity teams today.

A CISO-focused guide to governing agentic AI systems before autonomous decision-making introduces security, compliance, and operational risk.