
Exploring the Docker RESTful API with a Focus on Security
A comprehensive guide to the Docker RESTful API, its functionality, and critical security considerations for safe usage.
Explore the world of cybersecurity with in-depth articles and guides. From ethical hacking to threat defense, master the skills to protect digital assets.

A comprehensive guide to the Docker RESTful API, its functionality, and critical security considerations for safe usage.
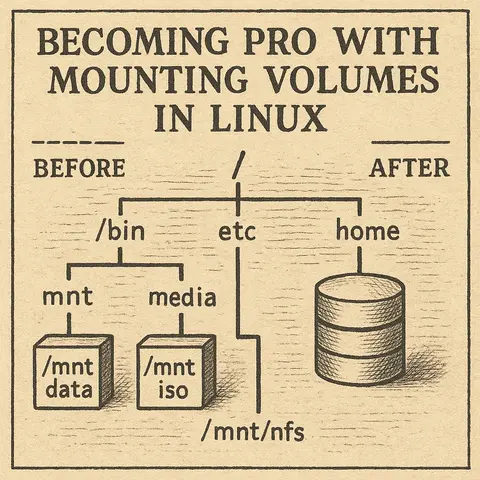
A complete guide to mounting volumes in Linux, starting from the basics and progressing to advanced scenarios with practical examples.

A detailed guide on what runbooks are, why they matter in IT and cybersecurity operations, and how they streamline incident response and system management.
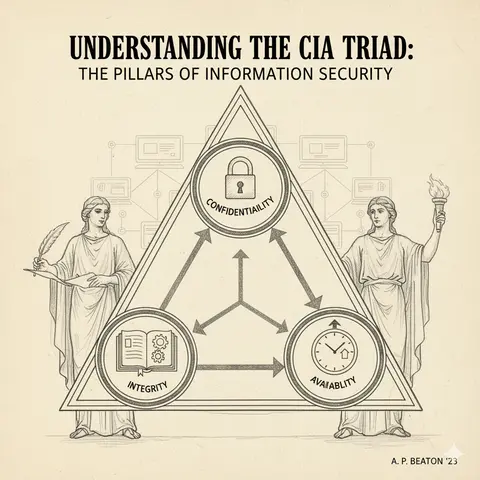
A beginner-friendly explanation of the CIA Triad—Confidentiality, Integrity, and Availability—and why it is the cornerstone of modern cybersecurity.

A deep dive into Near Field Communication (NFC), its applications in payments, security, and beyond, and what it means for businesses and consumers.
An in-depth exploration of object prototype pollution in JavaScript, from exploitation techniques to mitigation strategies.

A comprehensive guide to vulnerability management, focusing on using CVSS scores and exploitability metrics to prioritize patches effectively.

Struggling with inconsistent incident reports? Discover the essential elements of an effective Security Incident Reporting Template to ensure thorough, actionable, and compliant incident management. An example of a completed security incident report for AcmeTech Solutions.

A guide on how to properly document and report security incidents to ensure accountability, compliance, and effective response.
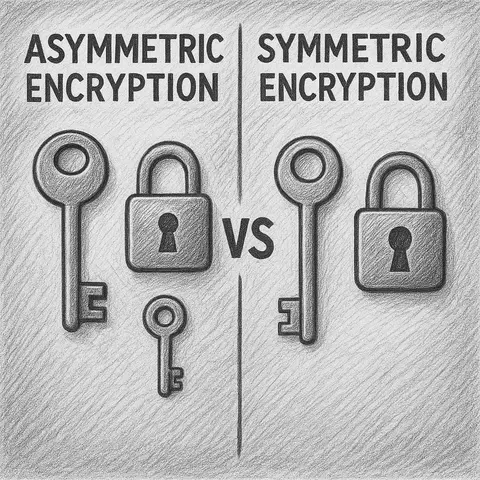
Learn the differences between asymmetric and symmetric encryption, their strengths, weaknesses, and how they impact modern cybersecurity. A clear guide for IT professionals and security enthusiasts.