
Getting Foothold in Cybersecurity: Techniques, Risks, and Defenses
A comprehensive exploration of the foothold stage in cybersecurity attacks, with red team techniques, code samples, and defensive strategies for blue teams.
Explore the world of cybersecurity with in-depth articles and guides. From ethical hacking to threat defense, master the skills to protect digital assets.

A comprehensive exploration of the foothold stage in cybersecurity attacks, with red team techniques, code samples, and defensive strategies for blue teams.

Learn what Data Loss Prevention (DLP) is and how it significantly improves cybersecurity. This article explains how DLP works with user stories and code examples to demonstrate its role in protecting sensitive data and ensuring compliance.
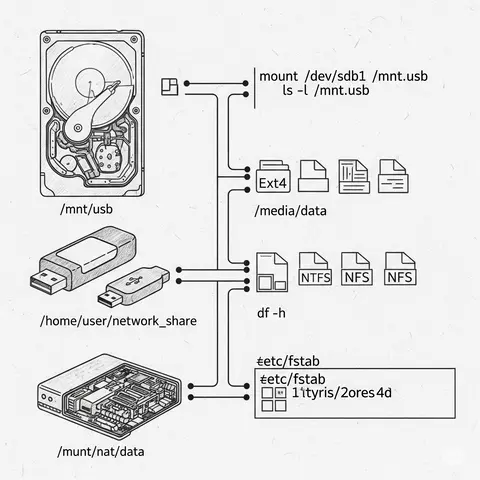
An in-depth red team guide to mounting devices and shares in Linux environments, including techniques for reconnaissance, exploitation, persistence, and stealth.
A comprehensive exploration of reverse shells, covering their core concept, red team usage, blue team defenses, and real-world implications.
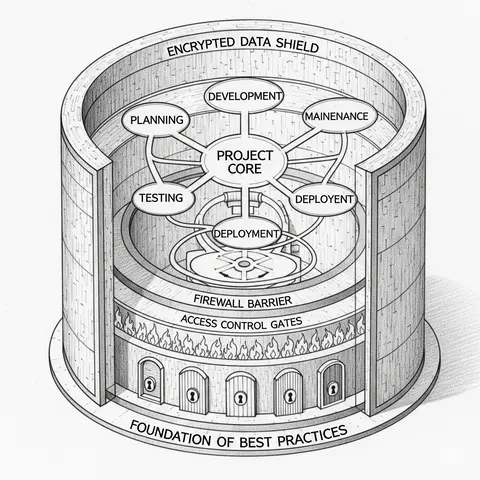
A detailed article exploring the principles and practices of building a secure project structure, illustrated with a case study.

A comprehensive guide to understanding Docker security threats and implementing best practices to defend your containerized applications.
A deep dive into how compression and archiving are used legitimately and maliciously, including real-world cyber attack techniques, red team tactics, and defensive measures.
A comprehensive guide to environment variables in Linux-like systems, exploring their legitimate use, exploitation techniques from a red team perspective, and defensive best practices for blue teams.

A deep dive into SIP attacks, their exploitation techniques, and red team methodologies for testing VoIP infrastructures.

A deep dive into defending VoIP infrastructure against SIP-based exploits, with actionable Blue Team strategies and technical detection techniques.