
Direct Drive Reads: A Double-Edged Technique in Cybersecurity
An in-depth exploration of Direct Drive Reads, their role in cybersecurity, and perspectives from both Red and Blue teams. Includes practical code examples and defensive strategies.
Explore the world of cybersecurity with in-depth articles and guides. From ethical hacking to threat defense, master the skills to protect digital assets.

An in-depth exploration of Direct Drive Reads, their role in cybersecurity, and perspectives from both Red and Blue teams. Includes practical code examples and defensive strategies.

Explore how geolocation plays a vital role in modern cybersecurity. Learn about its uses, risks, and how to leverage it to protect your data and network.

An exploration of how geolocation data is targeted by cybercriminals, the risks it poses, and the perspectives of offensive (red team) and defensive (blue team) security practices.
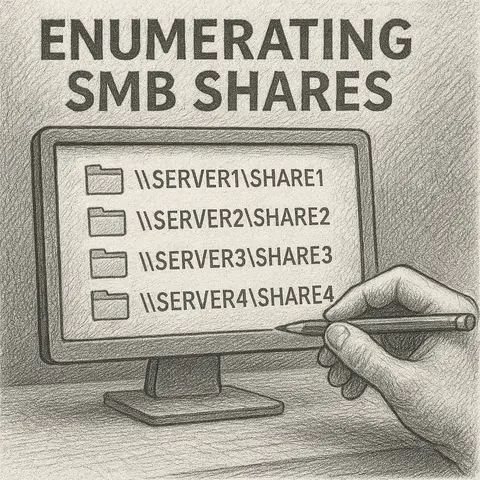
A technical guide on how to enumerate SMB shares using built-in tools and code samples. Learn how to use available scripts to perform SMB enumeration

Learn what Server-Side Request Forgery (SSRF) attacks are, how they work, real-world examples, and the best defense strategies to protect your applications from this critical web security risk.

Defensive coding style is about anticipating potential errors, edge cases, and unexpected inputs to make your code more robust, secure, and maintainable.
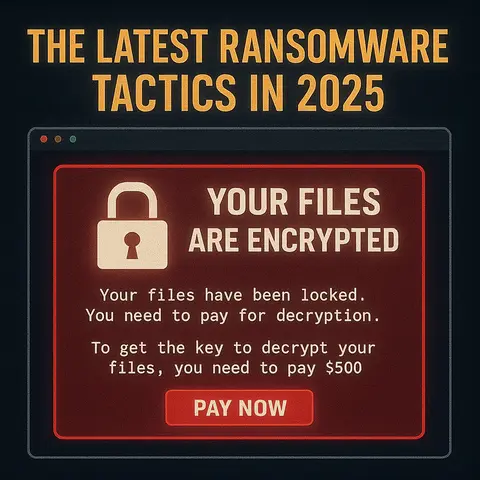
Learn the latest ransomware tactics in 2025, including double extortion, triple extortion, and new cybercrime trends targeting businesses worldwide."
Learn about SQL injection vulnerabilities and effective strategies to protect your web applications. Discover preventative coding practices and security measures to safeguard your data.

Explore how Active Directiry fits into a Zero Trust architecture, challenges enterprise face, and practical steps for secure identity management in hybrid evironment.
A beginner-friendly guide to computer memory and how cybersecurity teams use it to protect systems, detect threats, and investigate attacks.